Veriti research has found that over 25% of organizations allow bi-directional connectivity to and from the cloud without additional security inspection – a critical misstep that exposes businesses to cyber threats. Attackers are leveraging the cloud as a launchpad for malicious activities, exploiting the trust placed in these platforms.
Identifying Malicious Traffic from the Cloud
One of the biggest challenges for security teams is distinguishing legitimate cloud-based traffic from malicious activity. Threat actors commonly initiate attacks from cloud service providers, making it difficult to determine the true source of the attack. Security teams risk blocking legitimate business applications when trying to mitigate these threats.
Common misconfigurations include:
- Allowing SSH connectivity to cloud instances without proper restrictions
- Permitting SQL server connections from a broad scope, increasing exposure to potential attackers
These misconfigurations create easy entry points for cybercriminals, who exploit weak policies to breach cloud environments.
Cloud Based Attack Trends
Veriti research highlights that cloud providers are frequently used as launch points for cyberattacks, with Brute-Force, SSH, and Web App Attacks being the most common attack types.
Key Findings:
- Amazon, Google, Microsoft, and Alibaba Cloud are frequently used to launch cyberattacks against organizations.
- Brute-force attacks, DDoS, and SSH-based intrusions account for a large portion of threats coming from cloud providers.
- High-reputation threat actors (with a reputation score above 80) leverage cloud infrastructure to evade traditional security controls.
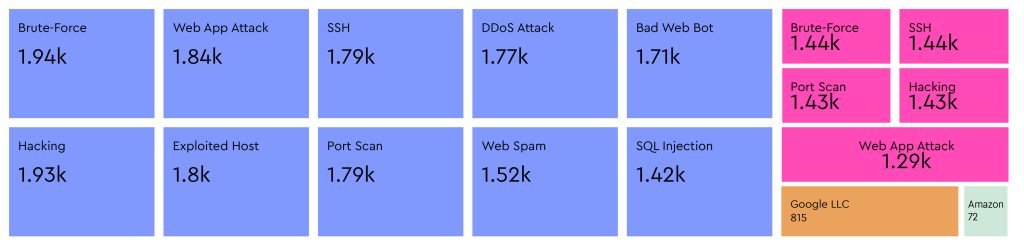
As seen in the data, Amazon Data Services, Google LLC, and Microsoft Corporation account for a significant volume of cyberattacks, with Brute-Force, SSH, and Web App Attacks leading the charge. Attackers take advantage of cloud resources to initiate large-scale attacks while masking their true origins.
The Evolution of Cloud Based Threats
While traditional brute-force and SSH attacks remain dominant, Veriti research has also identified new and evolving threats originating from cloud providers.
Emerging Threat Patterns:
- Port Scans & Exploited Hosts: Attackers are increasingly using cloud platforms for reconnaissance, scanning for vulnerabilities before executing full-scale attacks.
- SQL Injection & Web Spam: Cloud-based attacks are extending beyond brute-force methods to more sophisticated penetration techniques.
- DDoS and Automated Bots: Attackers are leveraging cloud resources to carry out large-scale DDoS attacks and deploy malicious bots at scale.
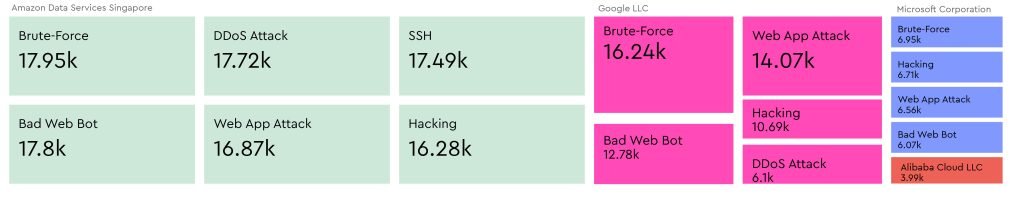
These evolving trends reinforce the need for proactive threat intelligence, strict security policies, and continuous monitoring to detect and prevent cloud-based attacks before they escalate.
To mitigate these risks, organizations must adopt a proactive cloud security strategy that includes:
- Restricting bi-directional traffic: Apply strict access control policies to minimize unnecessary exposure.
- Enhanced threat detection: Deploy advanced security analytics to monitor unusual activity from cloud sources.
- Zero Trust principles: Authenticate and verify all traffic before granting access to cloud resources.
- Regular security audits: Continuously assess and refine firewall rules and access controls.
The cloud is both an enabler and a risk. While it accelerates digital transformation, it also serves as a battleground for cybercriminals. Veriti’s research highlights the urgent need for organizations to reassess their cloud security strategies and adopt a more vigilant approach to threat detection and remediation.