Security teams today are overwhelmed – not just by the number of alerts they receive, but by the sheer volume of exposures across their environment. Despite the proliferation of dashboards, scanners, and risk scores, breaches still happen. The root cause often isn’t a lack of visibility – it’s misconfigured controls that go unaddressed for too long.
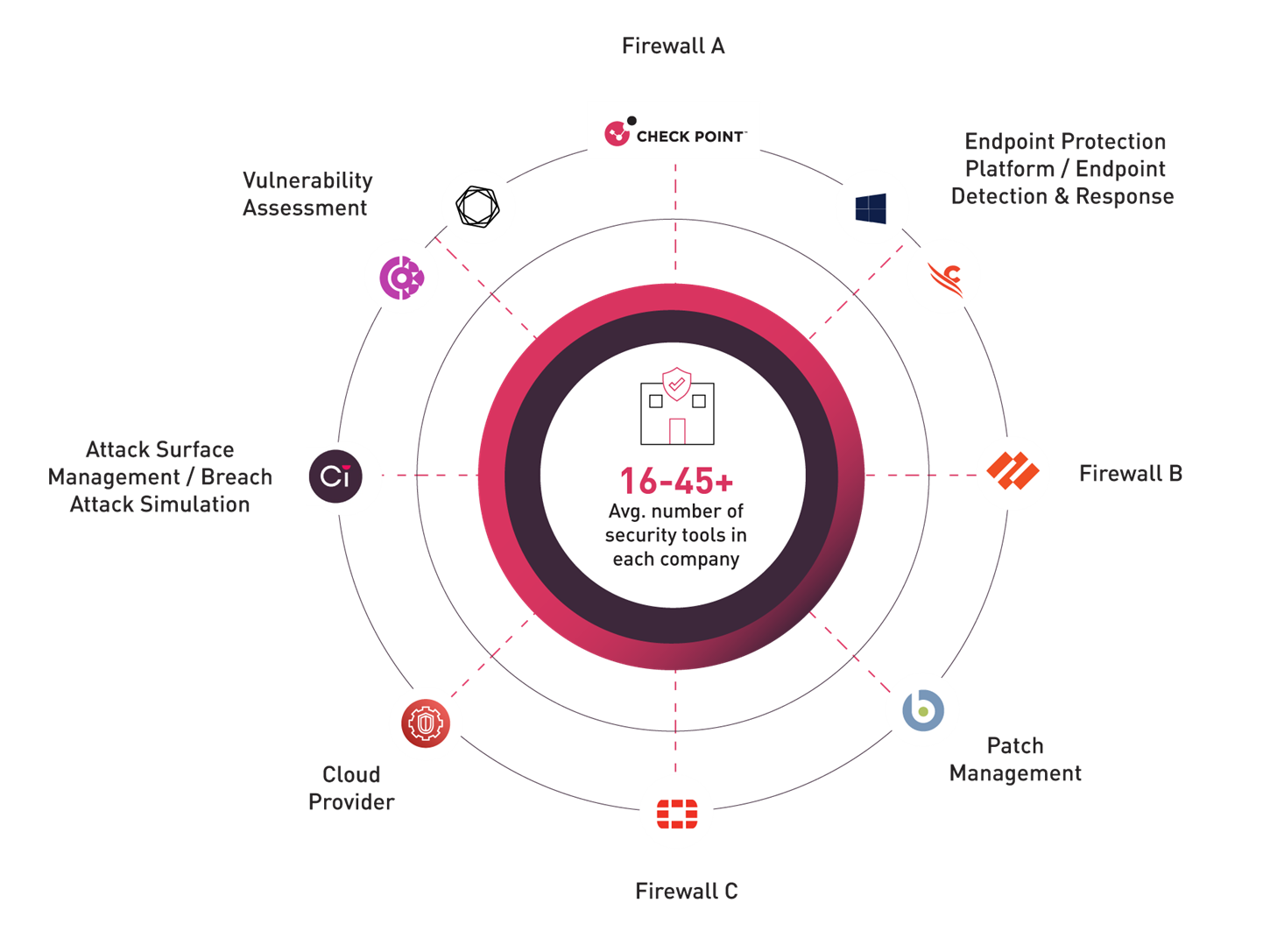
The problem is magnified by complexity. Most organizations operate with 16 to 45+ security tools, each collecting data in silos, each managed by different teams, and none fully aligned on what matters most. This fragmented environment creates blind spots and delays, leaving defenders struggling to keep pace with adversaries who are increasingly exploiting the gaps between tools, processes, and people.
And even when teams can identify risk, they often can’t act on it. The cybersecurity skills gap and alert fatigue make it nearly impossible to triage and remediate exposures at the speed threats demand. Analysts are drowning in data without a scalable, coordinated way to reduce real-world risk.
The Real Challenge: Who Owns the Fix?
Identifying risk is only part of the equation – someone still has to fix it. Yet this is where many organizations stall. Most tools tell you what’s wrong, but not who should take action. Teams are left asking: Who’s responsible for remediation? Who owns the fix? What’s the priority?
Meanwhile, not every vulnerability can – or should – be patched. Some exposures require mitigation, not disruption. Others require deep validation before changes can safely be made. Without clear accountability, prioritization, and action paths, exposure data becomes just another source of noise.
This is why we believe exposure management must be preemptive. Risk needs to be addressed before it’s exploited, and that requires a structured, automated approach to continuous discovery, prioritization, and remediation. It requires a platform built to support real-time action – not just insight.
Operationalizing CTEM with Veriti, a Check Point Company
CTEM is more than a framework – it’s a methodology to continuously reduce risk across the organization. But it only works when it’s automated, contextual, and built for action. Veriti fully supports all five CTEM phases: Scoping, Discovery, Prioritization, Validation, and Mobilization. Here’s how.
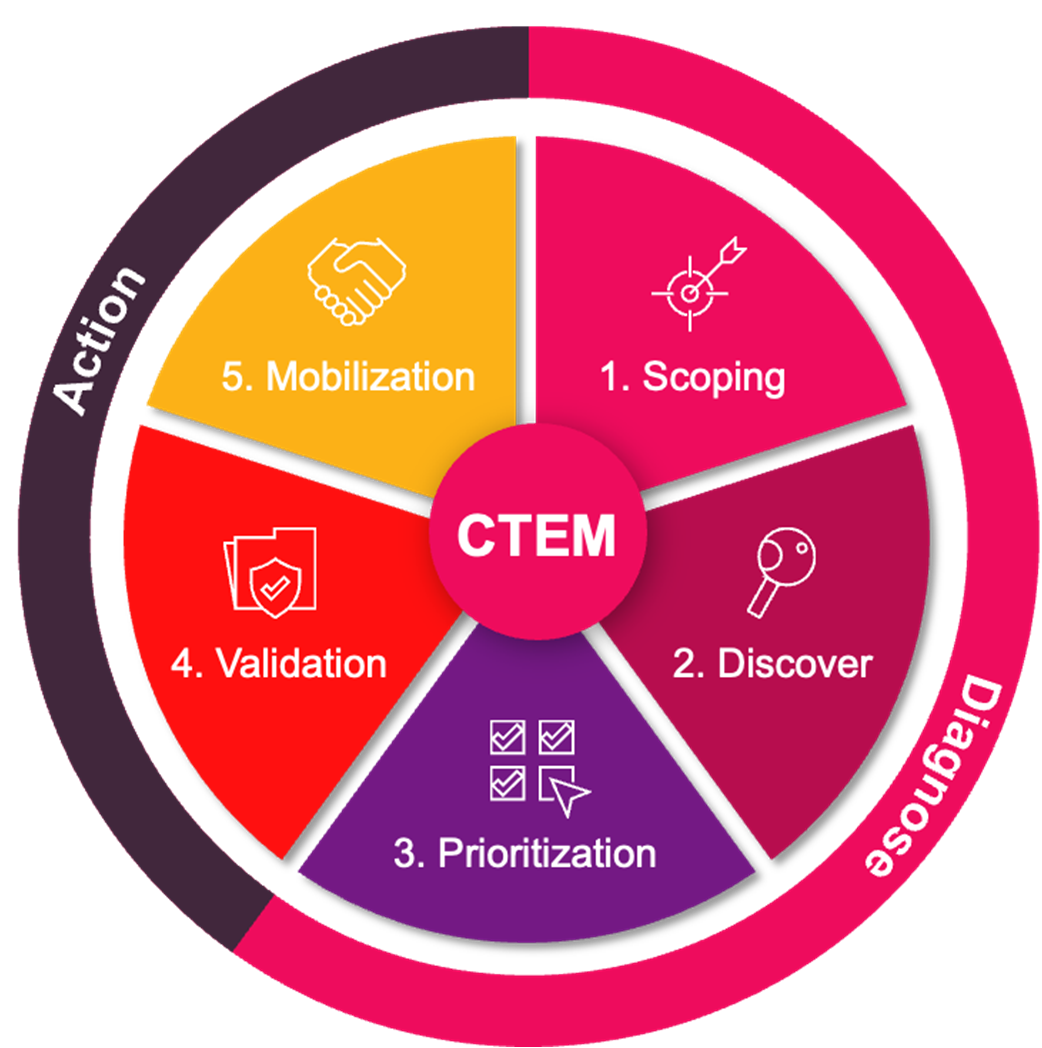
1. Scoping – Connect Across Your Ecosystem
Veriti integrates with over 70+ security tools – from EDR/XDR, firewalls, and vulnerability scanners to cloud platforms and ticketing systems. Integration is agentless and 100% API-based, enabling full visibility into your environment within minutes.
This integration power lets security teams see their real exposure surface in real time, across on-prem, cloud, and hybrid environments.
2. Discovery – Identify Exposures and Misconfigurations in Security Controls
Once connected, Veriti continuously assesses your environment for:
- Misconfigurations
- Control drift from security baselines
- Policy inconsistencies
- Detection logic gaps
- Ineffective enforcement
This real-time analysis gives teams actionable insights into what’s weakening their security posture before attackers can take advantage.
3. Prioritization – Focus on Business Relevant Risk
Veriti goes beyond CVEs and scores. Our platform evaluates:
- Exploitability
- Compensating controls already in place
- Business context
- Exposure level
This enables you to focus on the exposures that are most likely to impact your business – not just the ones with the loudest alerts.
4. Validation – Simulate Before You Fix
Not all fixes are safe. Veriti assess and validates all remediation paths to:
- Avoid operational disruption
- Eliminate false positives
- Ensure fix effectiveness
This lets teams deploy preemptive fixes confidently, knowing the outcome before making the change.
5. Mobilization – Remediate with Speed and Precision
With Veriti, remediation becomes a workflow – not a bottleneck. We support, non-disruptive virtual patching, adaptive IoC management and enforcement, security control hardening, and can safely remediate via direct APIs, SOAR, ITSM, and SIEM tools.
Our platform closes the loop – automating resolution across your tech stack, reducing MTTR, and maximizing ROI from your existing controls.
Why Preemptive Exposure Management Is the Future
We believe the future of cybersecurity isn’t reactive – it’s predictive, contextual, and preemptive. CTEM provides the structure, but it takes the right platform to make it real.
Veriti’s unique approach empowers security teams to:
- Eliminate exposure blind spots
- Prioritize what matters in business terms
- Act quickly and confidently, at scale
- Demonstrate measurable risk reduction – not just visibility
Whether you’re building a CTEM program from scratch or scaling an existing one, Veriti gives you the foundation to move faster than your adversaries.
Security is no longer just about finding problems. It’s about fixing the right problems, fast – and ensuring those fixes are safe, effective, and measurable. At Veriti, we’re here to help you do just that.