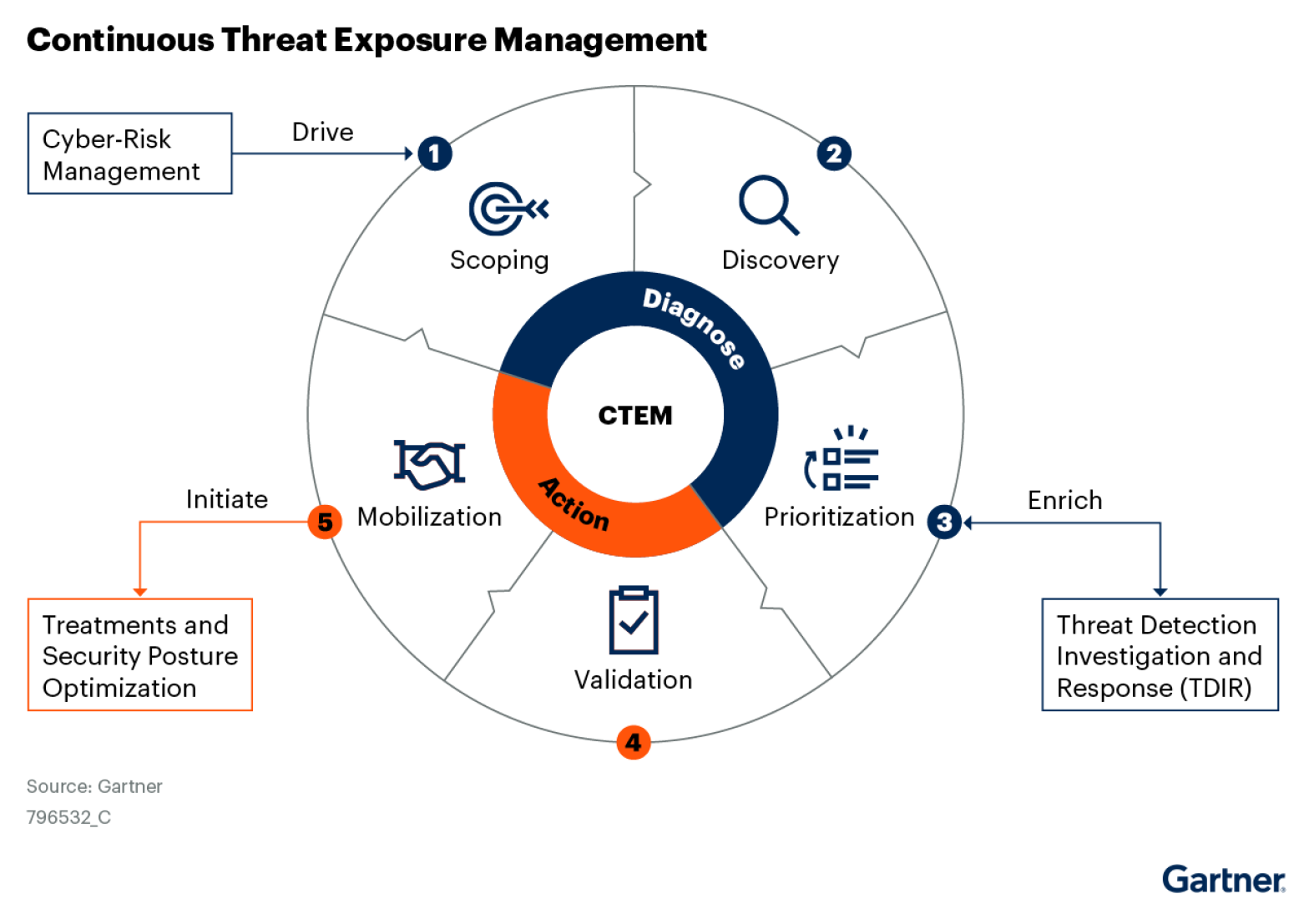
Effective vulnerability management has moved from a reactive process to a proactive, strategic imperative. Gartner 2024 report, How to Grow Vulnerability Management Into Exposure Management, says “Creating prioritized lists of security vulnerabilities isn’t enough to cover all exposures or find actionable solutions. Security operations managers should go beyond vulnerability management and build a continuous threat exposure management program to more effectively scope and remediate exposures.” Veriti’s Exposure Assessment and Remediation solution directly supports Gartner recommendations, addressing the core challenges of modern vulnerability management with an emphasis on integration, prioritization, and mobilization.
RECOMMENDATION 1
Gartner advises organizations to “define the scope and cadence of assessments, and articulate paths of remediation for identified exposures by consulting with department heads, product, and project owners.” We believe this approach encourages companies to establish an ongoing vulnerability assessment process that resonates with operational goals and aligns remediation strategies across all departments.
Veriti’s Approach:
Veriti provides a continuous Automated Security Control Assessment (ASCA). Veriti’s agentless approach leverages APIs for seamless integration with existing security tools, enabling comprehensive exposure monitoring without additional hardware or software. Through consolidating and correlating data from various sources, including VAs, BAS tools, and intelligence feeds, Veriti automatically identifies the root causes of vulnerabilities, security gaps or business disruption incidents for targeted risk prioritization. Veriti uses API-driven configuration changes and advanced machine learning to ensure corrective actions do not trigger false positives or cause application downtime, maintaining business continuity and operational integrity.
RECOMMENDATION 2
Gartner second recommendation is to “enhance discovery to include newer classes of assets, such as cloud and digital, and how this expanding attack surface affects the corporate environment and critical business processes.” We believe the expanding digital landscape, especially with cloud adoption, necessitates an inclusive approach to asset discovery.
Veriti’s Approach:
Veriti’s platform provides end-to-end visibility into both traditional and modern assets, covering cloud, digital, and hybrid environments. This integrated view is powered by Veriti Odin, an AI-driven assistant that enables users to visualize exposures across an organization’s attack surface, including cloud-based assets, mobile endpoints, and legacy systems. Veriti also integrates with CAASM solutions, enriching asset data with business context to capture the full scope of an organization’s vulnerabilities.
This comprehensive discovery model ensures that organizations have real-time insights into new asset classes, allowing security teams to understand the full scope of their attack surface and prioritize risk across all platforms.
RECOMMENDATION 3
To maximize the impact of vulnerability management efforts, Gartner recommends using “prioritization and validation to focus on actively exploited exposures and attack paths and to find the most cost-effective, multimodal way of reducing risk.” We believe this means going beyond static severity scores to consider factors like active threat exploitation, asset criticality, and cost-effective response paths.
Veriti’s Approach
Veriti’s prioritization model is built precisely to identify and prioritize vulnerabilities based on severity, exploitability, prevalence, and business impact. This framework leverages multiple metrics, including CVSS and EPSS scores, threat intelligence on active threat groups, and contextual information on affected assets. By analyzing all customer logs and correlating attacks with active vulnerabilities, Veriti elevates high-risk exposures in real-time, making them immediately actionable for remediation.
Additionally, Veriti offers advanced IoC management, aggregating and distributing IoCs across all security tools. This unified approach enables security teams to deploy countermeasures effectively, focusing on exposures with the most significant business impact. With Veriti, organizations can allocate resources efficiently, targeting vulnerabilities most likely to be exploited, without incurring unnecessary costs or disrupting critical operations.
RECOMMENDATION 4
Gartner recommends “Mobilize the treatment of exposures effectively by integrating with existing workflows and collaborating with non-security teams. Implement fixes using
predefined processes and agreed routes for prioritized business exposures. We believe this approach ensures seamless remediation, reduces downtime, and fosters cross-departmental support.
Veriti’s Approach
Veriti’s mobilization framework offers full integration with ITSM, collaboration, SIEM, and SOAR platforms. Security teams can initiate remediation actions directly through Veriti or use their preferred ITSM or collaboration tools to mobilize non-security teams. By connecting with these tools, Veriti ensures that tickets are automatically created, prioritized, and assigned, enabling rapid mobilization of security teams with minimal disruption to ongoing operations.
Veriti also supports automated workflows tailored to each organization’s needs. For example, Veriti’s “one-click remediation” option allows security teams to automate routine processes through ITSM, SIEM, or SOAR platforms, ensuring that remediation efforts are consistent and aligned with business goals. These integrations create an efficient, repeatable process that unifies stakeholders across departments, enhancing an organization’s overall response capabilities.
We believe that by adhering to Gartner recommendations, Veriti empowers organizations to go beyond basic vulnerability management, helping them build a resilient exposure management program that safeguards critical assets while ensuring operational continuity. Veriti’s approach allows security teams to proactively defend against emerging threats and align security initiatives with business objectives.
Gartner subscribers can access the full How to Grow Vulnerability Management Into Exposure Management report on the Gartner website.
How to Grow Vulnerability Management Into Exposure Management, Mitchell Schneider, Jeremy D’Hoinne, Jonathan Nunez, Craig Lawson, 8 November 2024
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product, or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designations. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.